By Sean Martin, Founder & Editor-in-Chief, ITSPmagazine
Nintex xchange Sessions Highlight the Value of Privacy and Safety and Business
The Nintex xchange conference that took place in San Diego certainly succeeded in its mission; customers and partners were able to connect, share ideas, inspire each other to change the way they look at their business, and challenge the status quo in intelligent process automation.
Major tracks covered included deep dives into the Nintex automated workflow products, governance over data and workflows, and migrating to intelligent process automation. Along the way, several customers and Nintex partners shared both their successes and lessons learned when it comes to deploying automated, intelligent workflows.
Shared Responsibility for Compliance in the Cloud
One of the sessions I found particularly interesting was Managing Compliance with No-Code Solutions. It was (and still is) especially relevant given all the hoopla these days surrounding privacy. Monica Bush — the Senior Technical Program Manager of Security & Compliance for Nintex — was one of the presenters and discussed how the company’s security program for its cloud-based solutions focuses first on protecting customer information.
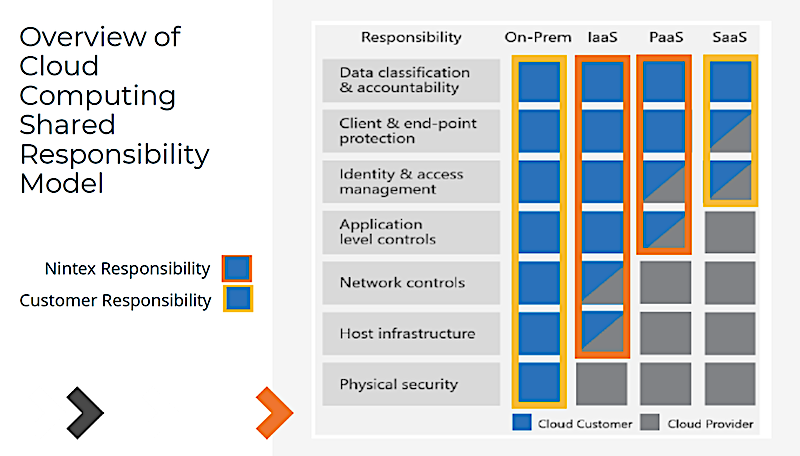
Customer data and workflows using Nintex solutions are hosted by world-class cloud service providers, but Nintex also takes responsibility for shoring up compliance for its customers by applying additional security elements. Bush covered how it’s important for customers to realize that there are these shared responsibility across the security spectrum among cloud hosting companies, cloud software providers, and customers:
Application-level controls
Network controls
The hosted infrastructure
Physical security of the infrastructure
Data classification and accountability
Identity and access management
Client and end-point protection
Depending on the environment — IaaS, PaaS or SaaS — the responsibilities shift, with customers assuming the most responsibility in an IaaS environment and the cloud provider taking the most responsibility in a SaaS environment. Nintex, as the application provider, also assumes its greatest level of responsibility in an IaaS environment (see table below).
Source: Nintex
To ensure the compliance of customer data and workflows, Nintex works only with cloud hosting providers who are SOC2-certified by the American Institute of CPAs (AICPA). Annually, AICPA attests to whether the Nintex cloud providers meet the SOC2 standards, and the program utilized by Nintex adheres to four key principles:
Trust based
Risk focused
Control effectiveness measured
Extensible with other compliance standards
Bush presented an example of how Nintex meets SOC2 criteria. One of the standards calls for procedures to end threats posed by security incidents through the closure of the vulnerability, removal of unauthorized access, and other remediation actions. To address this requirement, Nintex runs network and code vulnerability scans at regular intervals and remediates according to the SOC2 vulnerability management policy.
In addition, penetration testing occurs annually using an external service provider. The findings are remediated according to the Nintex vulnerability management policy. “You need to be able to drive actions for groups and individuals,” Bush says. “Accountability is key. We can see quarter-over-quarter how effective our controls are and that our workflows are operating together properly.”
Automating Incident Report Handling and Safety Requirement Tracking
Another intriguing session that had a direct human element attached to it was Safety First: From Incident Reporting to Safety Requirements and Tracking. Jesse McHargue of Duquesne Light Company and Trang Phan of The Boldt Company (a construction firm), presented how their companies are handling incident reports and tracking safety requirements.
McHargue explained how the manual processes that the company previously relied on required four hours per day of IT admin work. There was no reporting and data was incomplete. The company could not paint the full picture when it came to incident reports and safety requirements. This proved challenging in the day-to-day operations as well as during their routine safety reporting procedures.
To gain better control of incident reporting and safety requirement tracking, McHargue recommends automating processes, generating greater visibility and utilizing the cloud. By automating incident reporting and safety requirement tracking using a cloud-based Nintex automated workflow solution, Duquesne Light was able to defined standardized processes.
After converting from paper to electronic tracking, the company reduced admin time by 97%. Instead of sorting through what was essentially “three file cabinets of old data,” a simple electronic form takes away all the guess work.
With improved visibility and accurate data generated by the simple reports, Duquesne Light can also easily spot trends. “We now have the ability to efficiently identify safety concerns and safety strengths,” McHargue says.
This wouldn’t be possible if the systems and data were paper-based or only accessible in a physical office, as more than 60% of Duquesne Light’s employees work in the field. These employees want (and need) to do their work from anywhere and be able to process the same forms as those in the office. Therefore, a cloud implementation was critical for Duquesne Light to succeed with this program.
Automated Data Collection Helps Prevent Accidents from Reoccurring
Phan is a website developer for The Boldt Company. When someone gets hurt on the job, Boldt wants to make sure that they can collect the data surrounding the incident so it can be shared throughout the company in order to prevent the same accident from happening again in the future.
“We want to analyze and blend the data with other safety apps,” Phan explains. “We need to co-edit and look at pictures from smartphones and tablets to get the before-and-after view of what happened.”
“Using our cloud-based Nintex workflow solution with custom workflows designed for various devices, we take the data in, create a story in SharePoint, validate the story, and then publish it to the rest of the organization,” Phan says.
Streamlined Workflows Drive Data Privacy and Effective Business Processes
As the stories from these sessions illustrate, when it comes to ensuring compliance and protecting data in the cloud, an automated workflow such as those offered by Nintex offers a viable solution to solve the challenge. In addition to making sure data remains protected and that industry regulations are adhered to, you can significantly reduce the admin time of your internal IT team overseeing compliance and security.
About Sean Martin
Sean Martin is an information security veteran of nearly 25 years and a five-term CISSP. Sean is the co-founder and editor-in-chief at @ITSPmagazine and the president of imsmartin, an international business advisory firm. Sean's articles have been published globally covering security management, cloud computing, enterprise mobility, application security, InfoSec awareness and education, bug bounties, governance, risk, and compliance.